FaceBook Group Facebook Page
Showing posts with label how. Show all posts
Showing posts with label how. Show all posts
Sunday, February 26, 2017
How to Check Server Pokemon Go UP or DOWN
How to Check Server Pokemon Go UP or DOWN

One of the serious problems encountered due to the many people play the game Pokemon GO is inadequate server capacity. With so many people who play Pokemon GO, of course a few times we not able to get into the game as a result of server Pokemon GO sudden down and inaccessible
MMO Server Status is a site created in London. MMO Server Status will show whether the server Pokemon GO in various parts of the country is in trouble or not via the following link:
http://www.mmoserverstatus.com/pokemon_go
Latest :
Google Login 529ms
Poke Club Login 3hrs
Brazil 495ms
Germany 620ms
Italy 611ms
United Kingdom 497ms
United States 615ms
Argentina 582ms
Australia606ms
Austria496ms
Belgium494ms
Bulgaria490ms
Cambodia622ms
Canada498ms
Chile497ms
Croatia495ms
Czech Republic504ms
Denmark509ms
Estonia491ms
Finland496ms
France505ms
Greece499ms
Hong Kong ??495ms
Hungary499ms
Available link for download
Friday, February 24, 2017
How to Fix a MTP USB Device Driver Problem SURE WAY
How to Fix a MTP USB Device Driver Problem SURE WAY
I connected my Android phone to my PC and I heard the USB connection sound but my phone’s storages weren’t detected (both Internal and SD card). I checked under Device Manager and noticed that MTP had a warning icon (yellow triangle) on it meaning it had somehow malfunctioned.


The i try solving the problem by Downloading MPT (Media Transfer Protocol) Porting Kit from Microsofts official website yet it didnt solve the issue!
>>To Fix MTP USB Device Driver Problem
Go to Device Manager, under Portable Devices, right-click on MTP USB Device, and then click on Update Driver Software to update the MTP USB device driver.
>>Select “Let me pick from a List of device drivers on your computer”. The list will show installed driver software compatible with the device.
>>Select the driver you want to install and then click “Next”. Reconnect your mobile phone to your computer.
You will found out that is now working!!! :) dont forget to drop your experience in the comment box....
Available link for download
Sunday, February 19, 2017
How To Find Rare Pokemon Simple Method
How To Find Rare Pokemon Simple Method
![How To Find Rare Pokemon [Simple Method] How To Find Rare Pokemon [Simple Method]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEghTphsEI_E3nNDkVAnR6xdnNB10VdW4Vk-ZFbXbDz7K_VkdG2rVuBRN2XOyybCPj7WrEevJdgV8TeE-70pjah2lvcCbYJo1hTX-ltkPXxO-9dV-gaIntQ78KgeI0_9DC1auplHdGZNWsAL/s640/PokemonGo.RocketAPI.Console_2016-07-26_05-20-10.png)
How to Use
1. Download bot
2. Extrack Bot
3. Edit File User.xml. Than input your username & pass
4. Open bot
5. Go to pokesnipers
6. input pokemon name
7. Copy the link of those direction" the last part of it separated by / is the location of the Pokemon.
Example In my case it was : 40.788268154987, -73.968539742814
8. got it
Indonesia :
1. Download bot
2. Ekstrak botnya
3. Edit file user.xml , input username sama passnya
4. Buka botnya
5. Buka site pokesnipers.com
6. Masukin nama pokemonnya
7. Masukin letaknya
8. Dapet deh :v
See
[Bot PokemonGO] Download PokeCrot | New Update | Auto Bot Farmign Level UP Pokemon
How To Get UNBANNED From POKEMON GO !!!
Download PokeGOBot GreenGold Edition
If Succesfully :

PokeSniper2 1.7
Can now choose which Pokemon to catch based on catch list, minimum CP, minimum IV. Added Logging. Bugfixes
Download Bot v2.1.7
*update
PokeSniper2 1.8
Fixed API rate problem. Fixed autosniping Farfetchd and Mr.Mime. Added settings <ShowUsernameInTitle> and <CatchEverything> for the autosniper.
Download
Available link for download
Friday, February 10, 2017
How To Remove Pattern Lock Without Losing Data
How To Remove Pattern Lock Without Losing Data
Hello... Welcome to andro9ja

How to recover android lost password without losing data
Its been a while and we now guarantee you that we are back and better...Here today I present to you aroma file manager for managing files in recovery mode of any android device,remove pattern lock without losing data and
Recover your android lost password in just easy way... No loss more gain..
Heve you forgotten your Android device password and you want to unlockbit without losing Amy data..
Be rest assured you have come to the right place..
Below i will provide step by step guide on how to unlock your device.. Stay with me..
How to unlock android device with aroma file manager

Requirements...
- 1 Download Aroma File Manager here 1.35mb
- Your locked android device
- A memory card
- A battery charge up to 70%
- Backup your files (not necessary)
See also how to increase android internal storage
Procedures
- Download and move Aroma file manager to your memory card...
- Now boot your locked android device into recovery mode..
- Now goto install zip from SD card.
- Find and install aroma file manager from your memory card stick
- If you cant access memory card follow below steps
- Goto Mount and storage>> Mount Everything>> Mount System>> Mount data>>Mount afs>>Mount Preload>>Mount SDcard>> Mount ExternalSD>> go back>> Now Install zip from SDcard>>Choose zip from external SDcard
- After that an installation screen will appear and once its done.. You are good to go... Follow me...
- Once installation completes.. You will see prompt on the screen wetger to use the phones touch or the power buttons
- Not all phones recovery supports touch in recovery mode... To check if yiurs will work tapvthe no repeatedly and if it works aroma file manager will open..
- If it doesnt open, use the volume buttons to select yes and aroma file manager will open
- Now goto data folder >>system folder and find the gesture.key for pattern lock or password.key for pin lock.
- Long press the file for long and the option to delete will pop up..
- Delete the file and you are good to go.
- Now exist aroma file manager and restart your phone..
When you put on your phone,it will ask for a pin or pattern unlock code..
Enter any pattern or code and your phone will unlock..
But please no the the password or pattern you use... Now go and change your pattern or pin...
Conclusion
I hope you understand Above procedures Ive given.. You dont need going through the stress of losing your data just to unlock your smartphone...
If you have any complaints or help.. Please use the comment box below...
visit us again for more breathtaking updates...
Available link for download
Thursday, February 9, 2017
How to recover data from a damaged hard drive
How to recover data from a damaged hard drive

This is a complete guide hard drive recovery please stay tuned..
Damaging your hard drive is inevitable,if it doesnt happen to you, it might happenbto someone you know and we have come up with a perfect solution to help you out when the need arrives..you night also want you buy an external hard drive or a couple of handy ones to carry along wherever you go...
Here are vast range of solutions for you,if one fails you, the other wont...
Here lets begin...
1. Connect The Hard Drive To Another Computer
Before you can do any word on your crashed hard drive, you have to remove it, except if its an external hard drive then connect it to another machine..
Get a USB IDE/SATA adapter
If you are in Nigeria yiu can get one from jumia.com.ng or konga com.ng
They sell at affordable rates...
If you are in Nigeria yiu can get one from jumia.com.ng or konga com.ng
They sell at affordable rates...
Its cheap USB 3 adapter,affordable and above all faster in operation... I still prefer this though

If you dont have the adapter available then you then you could just connect it to another computer... This means pulling off another computers hard drive just to fix the broken one.. Make sure the computer detects the hard drive in its BIOS else it wont detect the drive once the computer boots up...
2. Try copying the data to another hard drive
Yes, after you have inserted the dameged hard drive in another system either internally or externally through USB sticks.. Try copying the files in the hard drive... Im sure yiu will be able to copy the user files cause only the operating system would be corrupt...
Copy the files you want to recover and you are good to go...
3. Download and try data recovery software
If yiu have tried the above steps and it all didnt work out.. Please download any of the recovery softwares that I will list below to sort tings out..
And please dont write or install anything on the corrupt hard drive else you risk overwriting and losing all your data...
Pc hard drive Recovery software #1
RECUVA

Get recuva recovery software here
The software is one of the vest outbyhere and also free.. Its from the makers of the popular Cc Cleaner...
Its simple and effective to use..
Even if the drive was formatted, recuva can scan and find its recovery files..
If the regular basic scan fails,yiu can try the deep scan that will see all hidden files..
Here is a portable version if you dont want to install the full version..
There is a wizard that will guild you through the processes
Also please enable deep scan if basic scan fails...
PC hard drive recovery #2
PC inspector file recovery

Click here to download PC inspector file recovery
This software is old but gold.. Use it if you are unable to recover your files with recuva..
Download and install...
Yiu will be asked to select your language please do..
The main menu has some options which are quiet interesting...
1. Retrieve deleted data : yes, this is how to retrieve deleted files from your hard drive.. Is easy and convinient ways...
2. Retrieve lost data : this helpsbyou recover data that were lost due to system crash or anything that might have happened..
3. Retrieve lost drive : and back to our main topic...this is the option we are here to talk about..it will search for the drive even though its not showing up in my computer and allows you browse its data...
Happy retrieving...
PC recovery software #3
Hirens Boot CD

Clich here to get hiren boot cd
This allows you to boot into a mini version of windows called Mini XP from the bootable CD or Bootable hard drive
And run diagnostic on a faulty computer..
Recuva is one of the Utilities that comes bundles with Hirens bootable CD..
Ensure you have a USB sticks so as to have a place to copy your files...
Now lets move on to Mac computers...
We have solutions for gat too..
See the solutions below..
Mac Hard Drive Recovery Software
MiniTool Mac data recovery

Yeah this is another awesome app but for Mac computers...
Click here to get MiniTool Mac Data Recovery
After download and install, you will see a screen prompt asking you to buy..
Well we all know nothing goes for free on Mac
After that you will find lists of options available...
Undelete recovery, damaged partition recovery,lost partition recovery,and digital media recovery.. Select whichever you want and you are good to go...
Thats all guys... Do come back for more updates as we explore the tech world together...
Available link for download
Friday, February 3, 2017
How to become a hacker updated part 2
How to become a hacker updated part 2
How to become a hacker
 |
| Hack just anything... |
Whenever we hear the word hacker and fear strikes, anger strikes in our minds. It is generally because a hackers are misunderstood in the society.
Not all hackers are bad, there are three types of hackers :
Black Hat | Bad Hacker
Grey Hat | Both Good And Bad
White Hat | Good Hacker
You have a choice to choose from the above then Follow and and fulfill your dream.
Operations system (basically Linux/UNIX)
After you have chosen what type of hacker you want to become... You have to learn Linux as an operation system.. Master it so that if will serve you in return...
A true hacker depends on freeware and open source.and Linux is the best to hack anything...A hacker must have a good knowledge of Linux Operating Systems like: Red Hat, Kali Liux, Debian, Back Box. Its very important to learn more than one Linux Operating System.


Programming...
It is important for a person in the hacking field to learn more than one programming. There are many programming languages to learn such as Python, JAVA, C++. Free tutorials are easily available online over the internet. Specifically in hacking field languages like C++, Python, SQL etc. are very important.
Cryptography
Now this is where the things get interesting, for you to stay safe,for your programs,files, documents and everything you do on the net to stay safe..you need the art of cryptography to prevent others from getting to you.. Look for cryptography tutorial over internet and learn it.
Networking concepts
You need to be good at networking concepts and understand how the networks are created. You need to know the differences between different types of networks and must have a clear understanding of TCP/IP and UDP to exploit loop holes in a system.
Understanding what LAN, WAN, VPN, Firewall is also important. You must have a clear understanding and use of network tools such as Wireshark, NMAP for packet analyzing, network scanning etc.
Learn a lot
Visit websites which teach hacking and networking exploitation signup on hacking forum ask help discuss with other hacker. Learn from expert hacker. Learn about phishing, sniffer, Trojans, RATs etc. Also learn good amount of batch programming and shell programming.
Practice
After learning few programming concepts or OS concepts sit and practice them. Set up you own Hacker Lab with a good system with good processor and RAM because your regular system won’t handle hacking too smoothly.
Find/write vulnerabilites
Vulnerability is the weakness or a loop hole or open door through which you enter the system. Look for vulnerabilities by scanning the system, network etc. Try to write your own vulnerability programs and exploit the system.
My advice
Practice and practice. As practice makes perfect... You can do it... But please dont do hacking to harm others or for fraudulent activities...
PART 2
Protection...
The keg to everything in life is protection. We protect ourselves, home,property,loved ones,family, our surroundings, you as a hacker need protection to avoid being caught...
Remember protection comes first...
In hacking industry most important thing is security, anonymity and protection. Play cool and be safe. There are numerous rules in the hacking area i’ll list few of them.
Don’t mess with government. You may be a great hacker but hacking government, is not a good idea they will hunt you with their best of best hacker and catch you so no government.
Don’t mess with big international level or rich company. Again the rich douches will bring you down.
Never hack or destroy a website supporting education for poor, home for poor or any program for backward countries, you will be a disgrace and other hackers will level you to nothing.
Don’t hack for personal gain. Fight for rights and seek information. Like Anonymous.
Methods of protection...
Don’t Use Windows
Windows is full of holes that can be exploited. These holes may allow spyware to infest, completely overcoming all your anonymity efforts. Any good hacker avoids Windows. Instead, they use security hardened open-source operating systems, such as Tails and Whonix.
Never Connect To Internet Directly
Connecting to internet directly means giving away your privacy by showing you IP.
Avoid anyone tracking down you’re real IP address through using VPN or Proxy. VPN enables users to create a encrypted private tunnel.
Anyone attempting to trace from the internet side can only see the address of the VPN server, which could be a server located in any country around the world you choose. Here is a tutorial telling what is Proxy and how to get one and use. Click here for the tutorial
Never Mail Using Your Real ID
Instead, use anonymous email services or remailers. Anonymous email services allow you to email someone without any trace back to you, especially if coupled with VPN or TOR access.
Remailers are a service whereby you can send from a real email account and the remailer will forward it on anonymously. To know how to send anonymous mail visit Here
Don’t Use Google
Google makes track everything you do in order to serve up adverts that you might click on. And as useful as the search engine is, there are ways to get the best out of it without compromising your identity. Services such as StartPage serve up google results but doesn’t store IP addresses, cookies or records of your searches. DuckDuckGo provides a similar service.
An Advice
Learning, is essential to hacking. You must first learn then hack. You cannot be lazy.
To become a hacker you also need to read a lot. It’ll take you around 2-4 years of learning to be a real hacker. If you think its too much you shouldn’t be a hacker.
You need to spend atleast 3-4 hrs a day with computers learning, I don’t think its too much computers are really interesting I spend my 2/3 of the day with a computer.
Tomorrow we will cover CRYPTOGRAPHY....and how to meet and talk with other hackers
Please stay tuned...
#TeamAndro9ja
Available link for download
Wednesday, February 1, 2017
How to upgrade infinix hot x507 to lollipop without pc
How to upgrade infinix hot x507 to lollipop without pc

Hi there.. Welcome to andro9ja.tk...
I use this device and I will do all my best in providing the best for other users like me..
Have you ever wandered if you could upgrade your infinix hot device without pc. You have searched the whole internet for solutions but nothing showed up...
Well you have come to the right place...
Follow me..
Please note that you must be on infinix stock recovery
If you are on stock recovery thats a good news... And if u are not.. Please get one as a custom recovery will get your device bricked..
Download Infinix Hot X507 Lollipop Final Tcard version from herehere
The update will dowoad via an app called mega... Dont worry if the link takes you to play store.. " that means you dont have the mega app installed"
After downloading the update and you have stock recovery installed...
What next.. Upgrade.... And enjoy the brand new user interface...
Feel free to ask questions... Im here for you...
Available link for download
Sunday, January 29, 2017
How To Change Nickname Pokemon Go
How To Change Nickname Pokemon Go

Now, you can change your nickname in-game. Heres how:
- Open Pokémon Go from your home screen or app drawer.
- Tap the red Poké Ball on the bottom of your screen.
- Tap the Settings button on the top right of your screen.
- Tap Change Nickname in the Settings list.
- Tap Yes to the question "Do you want to change your nickname?"
- Enter desired nickname. Tap OK.
- Tap Yes to confirm.
Policy :
How do I change my nickname or team?
Nickname changes
Nickname changes are only allowed for players that accidentally input their real name or other personally identifiable information as their nickname. Request a nickname change via the Help Center. Change requests currently take several weeks to review and process.
Team changes
Unfortunately, we are unable to change make team changes at this time.
Available link for download
Saturday, January 28, 2017
How to Enable Two Step Verification on WhatsApp
How to Enable Two Step Verification on WhatsApp

Technology giants such as Google, Apple, Microsoft, and Facebook among others have always advocated enabling two-step verification to add more security. If you still don’t use two-step verification, we recommend enabling the security feature following these simple steps for many popular services. Facebook-owned WhatsApp is the latest in the list of services to add support for two-step verification.
The new two-step verification is optional but your WhatsApp account is probably the one you want to secure first. The company assures that once two-step verification enabled, any attempt to verify phone number on WhatsApp will require the six-digit passcode that is created by the user.
Currently, the two-step verification feature is available only for beta users, we can expect it to be rolled out to all users in coming weeks. On Android, beta app users running version 2.16.341 or above will be able to enable the two-step verification. Windows 10 Mobile beta user, running version 2.16.280 of WhatsApp can enable the security feature.
To set up two-step verification for WhatsApp, you need to take the following steps:
To set up two-step verification for WhatsApp, you need to take the following steps:
Open WhatsApp (duh!)
Go to Settings
Go to Account
Look for Two-step verification
Tap on Enable
On the next screen, enter six-digit passcode.
Next, re-enter six-digit passcode.
Optionally, add your email address on the next screen.
Go to Settings
Go to Account
Look for Two-step verification
Tap on Enable
On the next screen, enter six-digit passcode.
Next, re-enter six-digit passcode.
Optionally, add your email address on the next screen.
In the last step – optional, as mentioned – WhatsApp asks for an email address to link with your account. This email address will let WhatsApp to send a link via email to disable two-step verification in case user forgets the six-digit passcode.
Remember that in case you user forget the six-digit passcode, WhatsApp won’t permit re-verifying the account within seven days of last using WhatsApp.
“After these seven days, your number will be permitted to re-verify on WhatsApp without your passcode, but you will lose all pending messages upon re-verifying – they will be deleted. If your number is re-verified on WhatsApp after 30 days of last using WhatsApp, and without your passcode, your account will be deleted and a new one will be created upon successfully re-verifying,” the WhatsApp team explains.
Have you set up two-step verification on your WhatsApp account? Let us know via the comments. For more tutorials, visit our How to section.
Available link for download
Wednesday, January 25, 2017
WhatsApp Video Calling Launched – How to Enable Whatsapp Video Calling on Android
WhatsApp Video Calling Launched – How to Enable Whatsapp Video Calling on Android

As we all know whatsapp is great social app and now a days million and millions users of different countries are using it on their android and windows phones. whatsapp is usually use to share photos ,musics,documentsetc. After a long time whatsapp release its new voice calling features and now two whatsapp users can talk to each other by using data network.
But now Whatsapp launched its whatsapp video calling features for testing and whatsapp users can do video call like Skype or Google Hangout etc. maybe you know or not you have to create a account on Skype and Google hangout for video call. But you no need to create any new account to use Whatsapp video calling.its just like same as voice calling feature.
In the past Whatsapp video calling is a most awaiting features for their users but now whatsapp launched its whatsapp video calling for their valuable users and anyone can enable whatsapp video calling on their smartphone.
How to make video call from WhatsApp-Whatsapp Video Calling
Making a video call from Whatsapp is so simple as like voice call. For whatsapp video call just open any contact and click on call button as you do for voice calling. Here you will get two different whatsapp calling options like whatsapp voice call and second for whatsapp video call. Just click on video call to make a video call with your contact person or family member.
WhatsApp Video Calling screenshot*****

Note : till now this whatsapp video calling feature is enable for selected countries and going on testing . till now it’s on beta version .But it’s better to prepare your android phone before it live and in future you will be first as soon as it will live for everyone.
How to get WhatsApp Video calling or How To Enable Whatsapp Video Calling feature?
Finally, the question is how you will get WhatsApp video calling on android phone?
As I told you still its on beta version and you need to download the latest Beta version of WhatsApp apk and install on your device and also share this post to your friend and ask him to do the same.
Download WhatsApp Latest version for Video Calling ,just watch the video and see how to enable whatsapp video calling on any android phone?
Whatsapp has been launched whatsapp video calling but still its not rolled out for everyone. But officially whatsapp has announced that it will be live very soon. So be prepare for WhatsApp Video Calling!!
Incoming Search terms
whatsapp video calling
whatsapp video call apk
whatsapp video call activation
whatsapp video call download free apk
whatsapp video call iphone
whatsapp video call ios
whatsapp video call download free for android
whatsapp video calling invite
whatsapp video calling launched
enable whatsapp video calling
Available link for download
Monday, January 23, 2017
How To Use SQLi Dumper v8 Crack Hashed Passwords Afterwards
How To Use SQLi Dumper v8 Crack Hashed Passwords Afterwards

( recommend using SQLi dumper on a rdp or vps or using a proxylist )
Step 1: Download SQLi Dumper
Step 2: Find Dorks, use a dork generator, or buy some privately made ones or paid dork gen. link to free dork generator
Step 3: Use the program I just told you about to also scrape some elite proxies.
Step 4: Open up SQLi Dumper. Now load your dorks to SQLI dumper by copying and pasting right here like this.

Step 5: Load your elite proxylist into SQLi by clicking the "Tools&Settings" Tab, Then "Proxy" Tab.Copy and paste your proxies.
Step 6: On SQLi Dumpers Main page where the dorks are. Click "Start Scanner". Wait for dorks to finish scanning and collect all urls for you. note: it will go even further then 100% dont freak out. i think it stops at 150% you can always stop when you think its collected enough dorks. For enough urls to get a good Database try having at least 2000-5000.
Step 7: Once urls are finished being collected click "exploitables" tab then click "start exploiter" wait for it to scan through all urls and find the exploitable ones.
Step 8: Once you have all exploitables go to "Injectables" tab and click "Start Analizer" wait for it to finish finding the injectables out of all the exploitables.
Step 9: When done You should now see all your injectables and the countries, where they are from and more info. highlight all your injectable & at bottom left where it says "Search ColumnsTables Names (MySQL and MS SQL) -enlarge it by clicking + symbol. make sure "email, password and user" boxs are checked, then click start. It will scan all your injectables for ones that have user email and password files. then all you need to do is look at them and match up ones that say 800,000 user and 800,000 passwords, that means you just found a good 800k Combo Database and you now want to go and Dump the data to text file (: ( it even says which files the passwords/usernames/emails are located )
Step 10: right click the injectable that had the the big Database on it and click "Go To Dumper"
Step 11: once in dumper click get database, once database appears click on it and click get tables, once tables appear click on the "user" table (sometimes has different name like "members") and click "get columns" wait for them to appear then check on "user and password boxes or email" then click "Dump Data" button and watch them all start dumping. If no database appears retry once or twice then just move on ( sometimes they just wont dump )
Step 12: after the long wait and you are finished dumping the usernames or emails ( or both ) and passwords you can now extract them to you desktop as a txt file. click Export Data and name the file and place it where ever you choose.
Example should look like this when exporting:

( note: there is thread options in each section ;) )
Cracking Hashed Passwords (MD5 Hashed)
Step 1: To crack passwords download, hashcat Click Here (choose hashcat binaries download) click on "v2.00" to download
EXAMPLE:

Step 2: Extract hashcat to a folder on your desktop using 7zip. Once extracted, go into hashcat folder and create 2 new .txt files and 1 new folder file. Name one .txt file "hashes" and the other "cracked". Name the folder "wordlists".
Step 3: Go get some wordlists to put into your wordlist folder. type "hashcat wordlist" into google and grab all you can (: any word or password can be used in your wordlist. make it nice and big lots of gigs if possible the more the better.
Step 4: Once you have wordlists in your wordlist folder you created, you are ready to start and try cracking. go grab a combo you got from SQLi Dumper that was hashed and copy and paste it into the "hashes.txt" file you created.
Step 5: open cmd by going to your start button on your desktop and click it then type "cmd" then right click the one that says cmd & open as administrator ( I needed to for my pc, you might not need to for yours )
Step 6: when the cmd window is open. first thing is type CD then click space. and drag your main hashcat folder right onto the cmd window then press enter.
hashcat.exe -m 0 --username hashes.txt wordlist.folder
( Blue color is what gets dragged not typed )
Step 7: cmd is now inside hashcat, if you are using a 32 bit PC drag hashcat-cli32.exe into the cmd window now. if you are 64 bit drag hashcat-cli64.exe instead. press space and type -m 0 --username press space and drag your "hashes.txt" over, press space again and drag your wordlist folder over into cmd windows as well. press space then enter it will start Cracking the hashed combo you had in your hashes.txt with the wordlists you have in your wordlist folder.
hashcat.exe -m 0 --username --show hashes.txt --outfile-format=2 -o cracked.txt
( Blue color is what gets dragged not typed )
Step 8: once it has finished. just keep cmd window open and again drag your 32 or 64 bit exe over first. then press space and type -m 0 --username --show press space and drag your "hashes.txt" file over press space and then type --outfile-format=2 -o press space and drag your "dehashed.txt" file over then press space and press enter. your combo should now appear in your cracked.txt file with the usernames:passwords dehashed (:
Step 9: If they look like a mess in the cracked.txt file, like "user:passuser:passuser:pass" then just download Notepad++ Click Here
and open notepad++ and copy and paste the cracked.txt file combos into notepad++ and they will all look all in neat order now (: then just click save as and save it as something new and it will come out as user:pass Instead so you can now run it on a combo checker.
user:pass
user:pass
Files
SQLi Dumper v8
dork_maker_3xploi7.rar | Pass : 3xploi7
Hash Cat
Available link for download
Sunday, January 22, 2017
New Rs 50 Rs 100 Rs 1 000 Notes Design Security Features How To Exchange Old Currency
New Rs 50 Rs 100 Rs 1 000 Notes Design Security Features How To Exchange Old Currency
New Rs.50, Rs.100, Rs.1,000 Notes Design
The lower denomination currency notes of Rs 100 and Rs 50 will hang in as a valid currency in the circulating medium. Economic Affairs Secretary Shaktikanta Das stated that edification and improvement in the appearance of currency notes of Rs.1,000, Rs.100, Rs.50 denominations will be executed. The new notes of Rs.2,000 are being issued because of unpredictable inflation rates. Banks and post offices have already started issuing the new series of Rs.500 and Rs.2,000 notes. The Reserve Bank of India will also bring new possible changes in Rs.50, Rs.100, Rs.1,000 Notes.

New Rs.50, Rs.100, Rs.1,000 Notes Release Date
The government on Tuesday had withdrawn the use of old Rs 500 and Rs 1,000 notes to whitewash black money and terror financing. The colour new Rs. 500 note is stone grey and approximately will be in size of 66mm x 150mm. Newly shipped Rs 2,000 notes will be of magenta colour with Mangalayan designated on the reverse side. The new banknotes of Rs 500 and Rs. 2000 are distinctive in the premises of series in colour, size, theme, a ground of security features and design element. The Reserve Bank of India is going to bring forward Rs. 2000 denomination banknotes in relevance to Mahatma Gandhi (New) Series. It will delineate the Image of Red Fort with Indian flag on the reverse side.
New Rs.50, Rs.100, Rs.1,000 Notes Features
New Rs.50, Rs.100, Rs.1,000 Notes with the new specification, Design and Security Features can act as the prime regulator of black money. The signature in all the new notes Rs.50, Rs.100 and Rs.1,000 will be of Dr Urjit R. Patel, Governor of RBI. A semblance of Swachh Bharat Logo with the printing as 2016 will be lithographed on the Banknote. In order to protect a country from the excessive supply of money government of India has come in active mode. Proposal to allow all foreign institutional investors in commodity trading has been left for the official decision. SEBI has been imparted with the duty to look into this proposal to define its scrutiny.


To know job updates in FaceBook
Available link for download
Friday, January 20, 2017
How To Hack Facebook Account With Facebook Remote Access
How To Hack Facebook Account With Facebook Remote Access
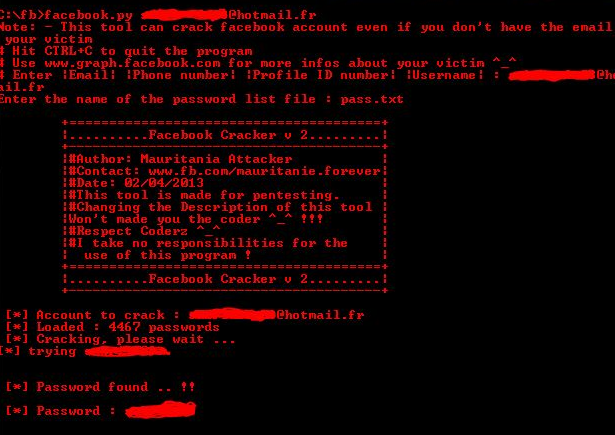
How To Hack Facebook Account With Facebook Remote Access - Hello 3xploi7er, today im going to share a trick that is very rare. Do you know token? token is a tool that is used user authentication. token is used to validate yourself and to a secret key.
On Facebook. This token have access to post an article, photo or link. But this token can be very fatal if other people know your token. Thus the token is very important and confidential. Do not let others know your facebook token .
Straight to.
Material :
Facebook Remote Access
HTC Oauth
Access Token
1. First we have to come here first: HTC Oauth
2. just Click ok, ok, ok ok ok
3. take your token : Access Token (See picture)
4. Copy your token
5. Paste the token on Facebook Remote Access (See picture)
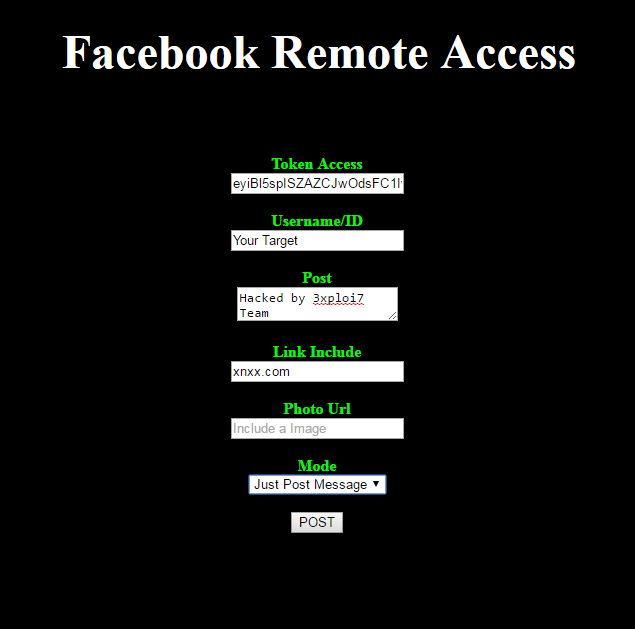
6. enter username, post, photo link url and others.
7. Select Mode, just post a message / Post link / Post Photo.
8. Click Post
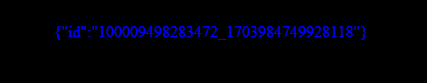
If Successful: { "id": "100009498283472_1703984749928118"}
== Indonesia ==
Di facebook. token ini mempunyai akses untuk memposting sebuah artikel, foto ataupun link. Tetapi token ini bisa sangat fatal apabila orang lain tau token kita. Maka dari itu token sangat berperan penting dan bersifat rahasia. Jangan sampai orang lain token facebook kita.
Langsung saja.
Bahan :
Facebook Remote Acces
HTC Oauth
Acces Token
1. Pertama kita harus kesini terlebih dahulu : HTC Oauth
2. Click ok, ok, ok ok ok
3. lalu ke akses token kita : Acces Token ( Lihat Gambar )
4. Copy token kamu
5. Paste token di Facebook Remote Acces ( Lihat Gambar )

6. masukan username, post, link photo url dan lain lain.
7. Pilih Mode, Hanya post pesan / Memposting link / Memposting Foto.
8. Klik Post
Jika Sukses : {"id":"100009498283472_1703984749928118"}

! Refrence
Remote Facebook Access Token Exploit
EDB-ID: 37185
Author: Jeremy Brown
CVE: N/A
Type: webapps
Platform: Hardware
Vulnerable App: N/A
Video Youtube
https://www.youtube.com/watch?v=bVr3BWCkLlI
3xploi7 Team
Available link for download
Subscribe to:
Posts (Atom)